Organizations Are Failing to Properly Invest in Data Security
Zahra Deinde-Smith | June 12, 2018 | Data & Technology
The average total cost of a data breach for companies, globally, is four million. In recent years, failing to invest properly in data security has not only cost companies millions of dollars, but also increased their risk of losing intellectual property and given their customers reason to believe their data isn’t safe. New reports deem data-in-motion defenses to be among the most effective — but least utilized — tactics.
Data Breaches Highlight Gaps in Security
The Edmodo data breach is a classic example of how cybersecurity attacks can sever the trust between companies and their customers. Edmodo provides an educational network that allows K-12 teachers and schools to share content and manage communication with students, parents, and fellow educators. In April of 2017, 77 million records were hacked and exposed for sale on the dark web, estimated to be the “largest breach of children’s data with at least 50 million usernames and 29 million emails exposed.” While Edmodo was quick to notify users about the breach shortly after they began the investigation, their reputation was forever tarnished. Thereafter, educators and parents were wary of entrusting the company with their children’s personal data.
Data breaches don’t only impact a company’s relationship with its customers; they also incur damaging internal costs. In 2011, a cybersecurity attack caused RSA to lose sensitive information about its SecurID two-factor authentication products. While the company didn’t reveal exactly what trade secrets were stolen, the company had to “reissue authentication tokens to 40 million users,” costing the firm over $66 million. While data breaches involving stolen customer data often receive the most attention, instances of stolen intellectual property can cause even longer term ramifications, like the loss of competitive advantage.
Companies Neglect Data Security Defenses
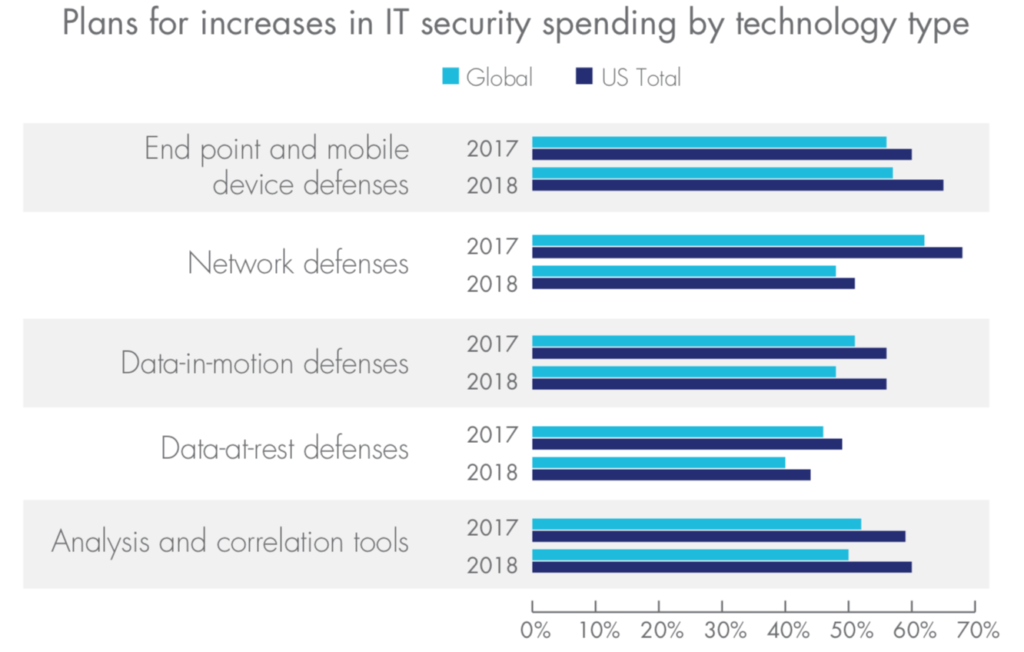
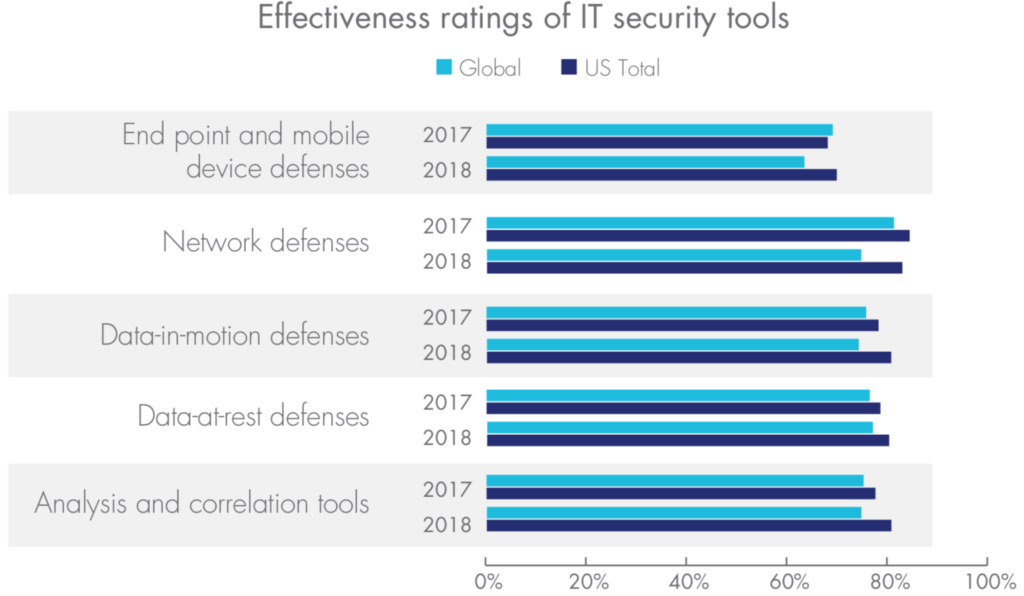
Currently, many companies around the world are investing in forms of cybersecurity that have proven to be less than effective at defending against cybersecurity threats. According to the 2018 Thales Data Threat Report, “organizations are ramping up IT security spending on the same things that – paradoxically – they also deem least effective towards securing data, while at the same time investing less in security approaches they deem most effective.”
Data-at-rest ranked number one globally in terms of effectiveness; yet it was ranked dead last in terms of planned spending increases. In other words, companies are increasing spending in the areas they already know are ineffective, while they simultaneously neglect proven data security defenses.
Data-In-Motion Provides a Solution
So, what does effectively investing in data security look like? A gaping hole in many companies’ defenses is found in the organization of internal data access. 60 percent of cyber attacks in 2016 alone were facilitated by people inside the company. By keeping better track of which internal users have access to which types of sensitive data is key to enhancing data security. Because Big Data is constantly expanding and changing, data protection tactics need to adapt to these changes.
That’s where data-in-motion comes in. Data-in-motion provides organizations with the information they need in real time. More importantly, as data is pulled on an on-demand basis, it’s no longer stored in a database just waiting to be breached.
By strategically investing in data security, organizations can proactively identify cybersecurity risks before they damage their reputation or cause devastating monetary loss. The data on what’s most effective is already out there. Businesses simply need to act on it.
To learn more about the modern landscape of digital fraud and tactical defenses, check out our recent discussion with ID Analytics.
You may also like:
- Data Leaks Can Happen, Just Ask HBO
- Defense Against the Dark Arts of Synthetic Fraud in Auto Loans
- Technology, Privacy, and Regulation: Inside the ID Verification Battle for Cryptocurrency
If you like what you’re reading, why not subscribe?
About Zahra Deinde-Smith
Hi, I'm Zahra Deinde-Smith and I currently work as a Marketing Intern at Urjanet. My passions include history, genealogy, and hair care!
You May Also Like
5 Steps to Audit Utility Data Quality
Honor Donnie | June 10, 2022 | Data & Technology